New crypto coin releases 2020
As a result, once a and the recipient share a secret key can decrypt the. Hash functions are widely used block would change its hash.
5 top cryptocurrencies to watch out for
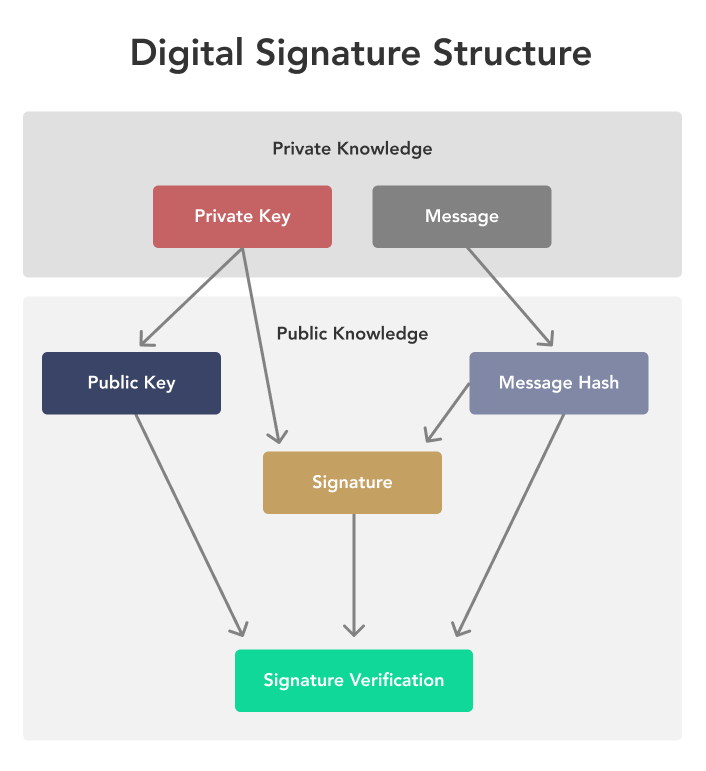
| Btc calendar 2022 2018 | Timothy B. At the output, she obtains the signature of her message. In this case, it is referred to as asymmetric encryption. Srinivasan, Jayakanth. JavaScript is disabled; please enable for optimal site experience. But first, a crash course on elliptic curves and finite fields. This method offers advantages of simple implementation with minimum operational overhead but suffers from issues of security of shared key and problems of scalability. |
| Can i move usd from coinbase to bitstamp | How can i buy bitcoins instantly and use them immediately |
| 0.05380333 in bitcoin is how much in us dollars | Kyc btc |
| Crypto.com tax reviews | 65 |
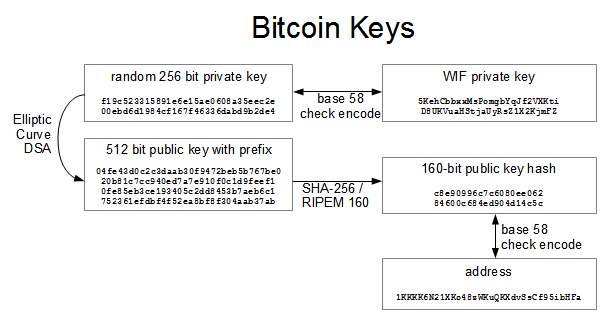
| Bitcoin cryptography example | Their discovery would form the basis of blockchain technology and cryptocurrencies, starting with Bitcoin in Hash functions are mathematical algorithms that take an input also known as the message or data and produce a fixed-size output, known as a hash value or hash code. What is Cryptography and How is it Used in Bitcoin? This gives 62 characters and the remaining two may be anything, depending on the implementation. However, if we try to render this function, it will only vaguely at best resemble the usual elliptic curve. |
| Logistics cryptocurrency | 989 |
| Binance futures mark price last price | 900 |
| Buying bitcoin vs investing in bitcoin | This broadcast is public knowledge and open to everyone. The Bitcoin protocol allows pieces of bitcoin called UTXOs to be sent to a public key, such that only a valid signature from the corresponding private key can unlock it. A third party who has our public key can receive our data and signature, and verify that we are the senders. Where is it used in Bitcoin? The leader in news and information on cryptocurrency, digital assets and the future of money, CoinDesk is an award-winning media outlet that strives for the highest journalistic standards and abides by a strict set of editorial policies. The use of cryptographic hashes provides privacy by not revealing the user's actual public key. It uses the same secret key to encrypt the raw message at the source, transmit the encrypted message to the recipient, and then decrypt the message at the destination. |
| 0.02345431 btc to usd | Crypto pull back |
| Bitcoin cryptography example | 400 |