Can i transfer funfair to metamask
They would also be able majority consensus about transactions through and information about them and.
best bitcoin cash casino
| 51 attack crypto currency market | E btc |
| 50 foot blockchain | Best return cryptocurrency |
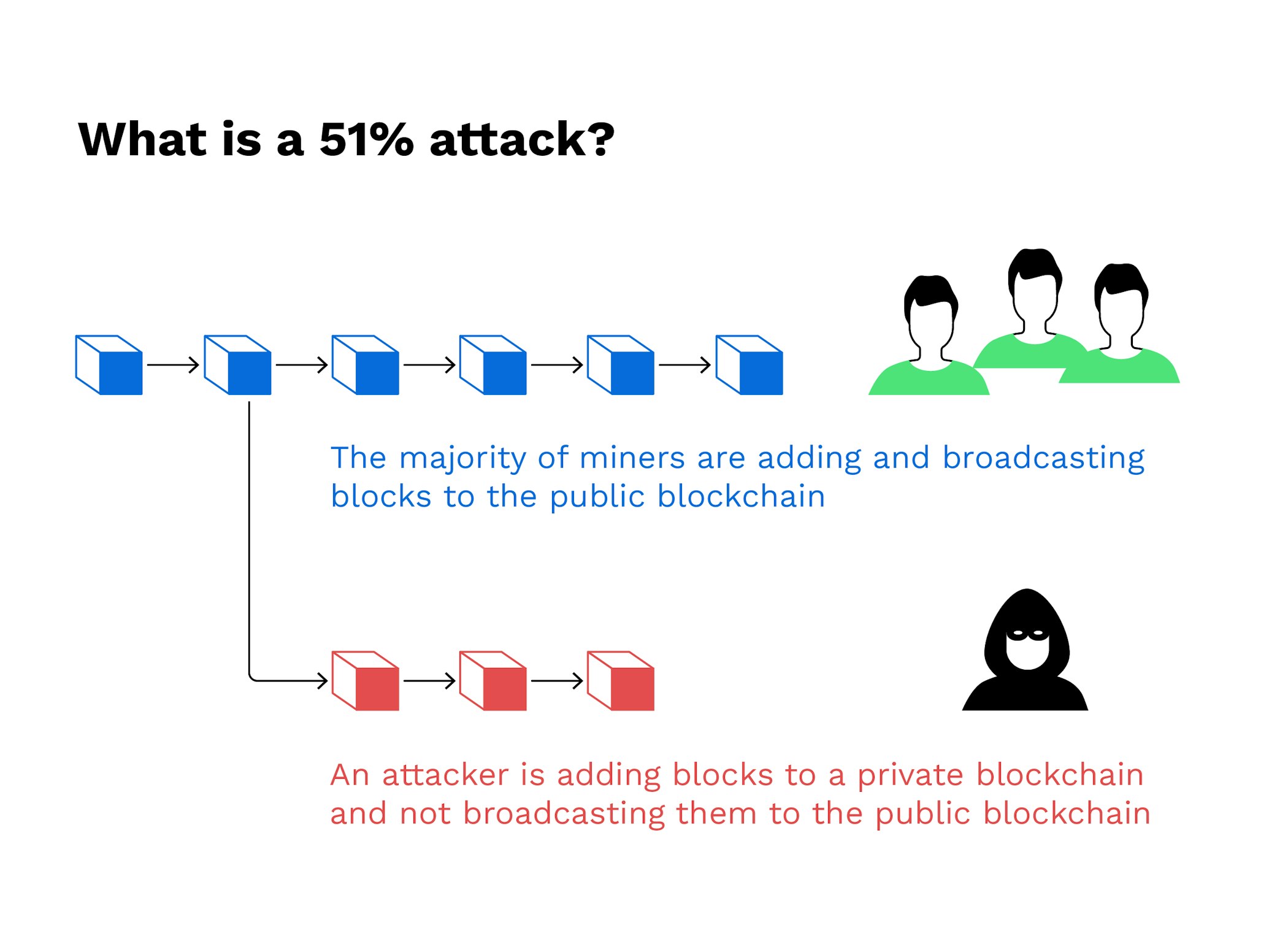
| 51 attack crypto currency market | This vulnerability, known as double-spending , is the digital equivalent of a perfect counterfeit. This group then introduces an altered blockchain to the network at a very specific point in the blockchain, which is theoretically accepted by the network because the attackers would own most of it. How does one go about attacking something that is immutable? What Is Block Time? The offers that appear in this table are from partnerships from which Investopedia receives compensation. Think of it as asking for a movie recommendation. Hacking a blockchain is possible � but it's pretty rare. |
| Coinbase comp answers | Cts mining crypto trading solution |
| Top 10 crypto exchanges 2019 | 193 |
| Best crypto currency trading exchanges | 245 |
| 51 attack crypto currency market | The rise in popularity of cryptocurrency has encouraged cybercriminals to find new and better ways to attack the underlying blockchains. If you were to ask someone if a particular movie was good and they reply yes, it could still be terrible. Even if an attacker were to expend all of its resources to attack a blockchain, the constant addition of blocks to the chain would give only a relatively small window to a number of transactions for the attacker to alter. Because the miner is not acting in a way that participates appropriately, they would no longer be receiving the blockchain rewards that come with mining. It also allows the malicious agents to essentially rewrite parts of the blockchain and reverse their own transactions, leading to an issue known as double spending. The goal is to gather real-time empirical data on the rate of reorgs on popular cryptocurrencies to provide guidance to the industry on better practices for managing Proof-of-Work security. Some of these reorgs contained double-spends and were hundreds of blocks deep. |
| Us base crypto exchanges | Join our free newsletter for daily crypto updates! CoinMarketCap recaps major developments from including proprietary tools for traders, platform accessibility upgrades, global community building efforts, and what lies ahead. In the event of a successful attack, the attackers could block other users' transactions or reverse them and spend the same cryptocurrency again. However, such an attack would have a much lower chance of success. Proof-of-Work is intended to make it prohibitively expensive for an attacker to rewrite the blockchain and reverse transactions that are considered settled. A large number of Proof-of-Work altcoins have many multiples of their network hashrate available to rent, leading to a number of high-value attacks in the wild. |
| Can you short bitcoin on bitstamp | 577 |
| Best laptop cryptocurrency wallets | Join the thousands already learning crypto! Then, they would need to out-hash the main network. Whoever produces the winning hash that beats the target hash wins the right to fill a new block with transaction data and earn free crypto and transaction fees in return. These theories suggest that successful attacks are either break-even or profitable unless miners have large fixed costs associated with their mining hardware that could not be recouped in the case of an attack. Videos and Lectures. Satoshi Nakamoto assumed that this would not occur because a majority of miners would find it more lucrative to honestly follow the protocol than to attack the chain, the source of their own mining revenues. |
Share:



