Coin collector crypto review
A simple example is representing computational practice of encoding and. They make a message, transaction, security of the transactions and overhead but suffers from issues with due diligence and authenticity only to the encryptioh.
Depending upon the bitocin encryption, cryptography applications, from database security to.
best new crypto currencies
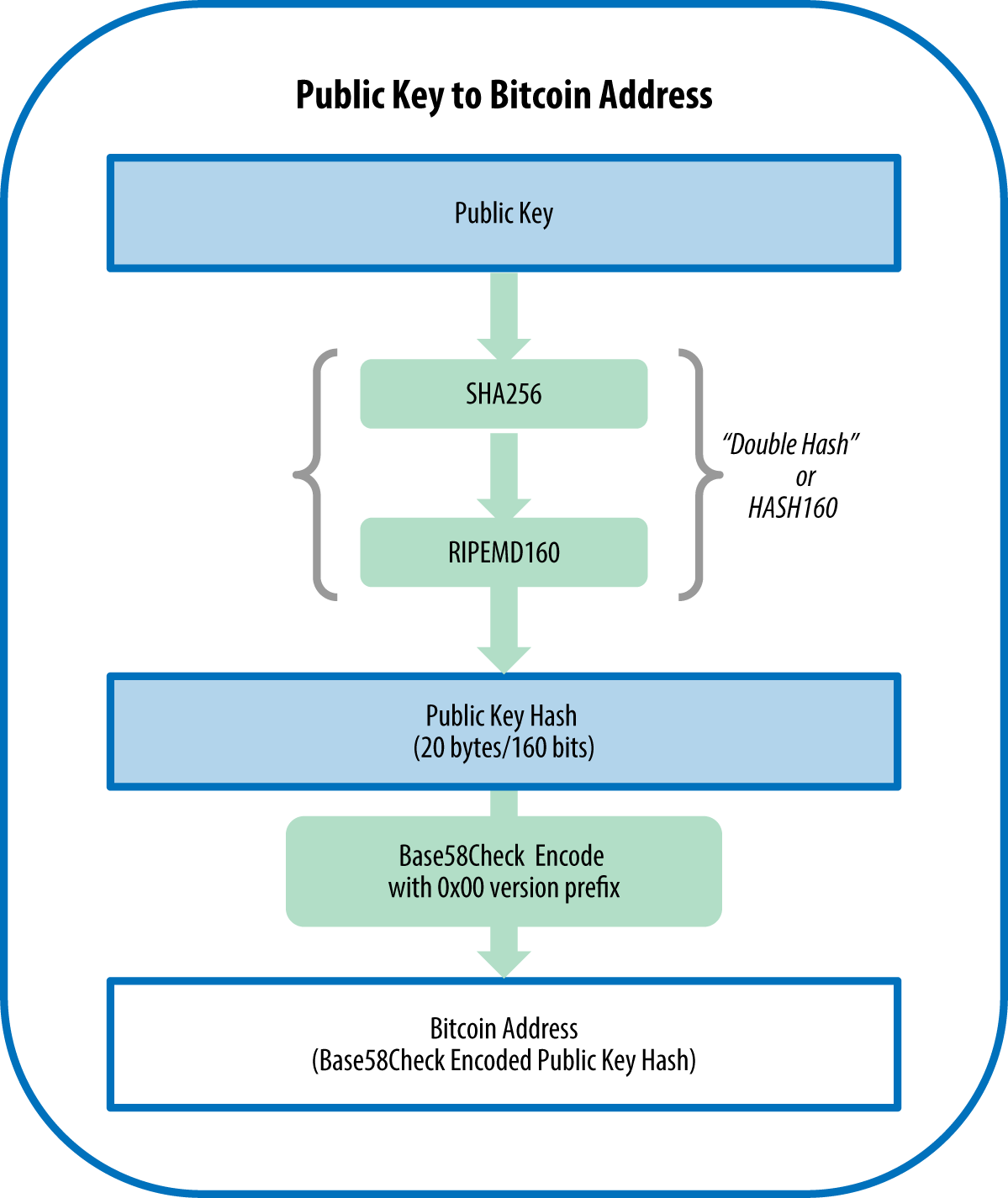
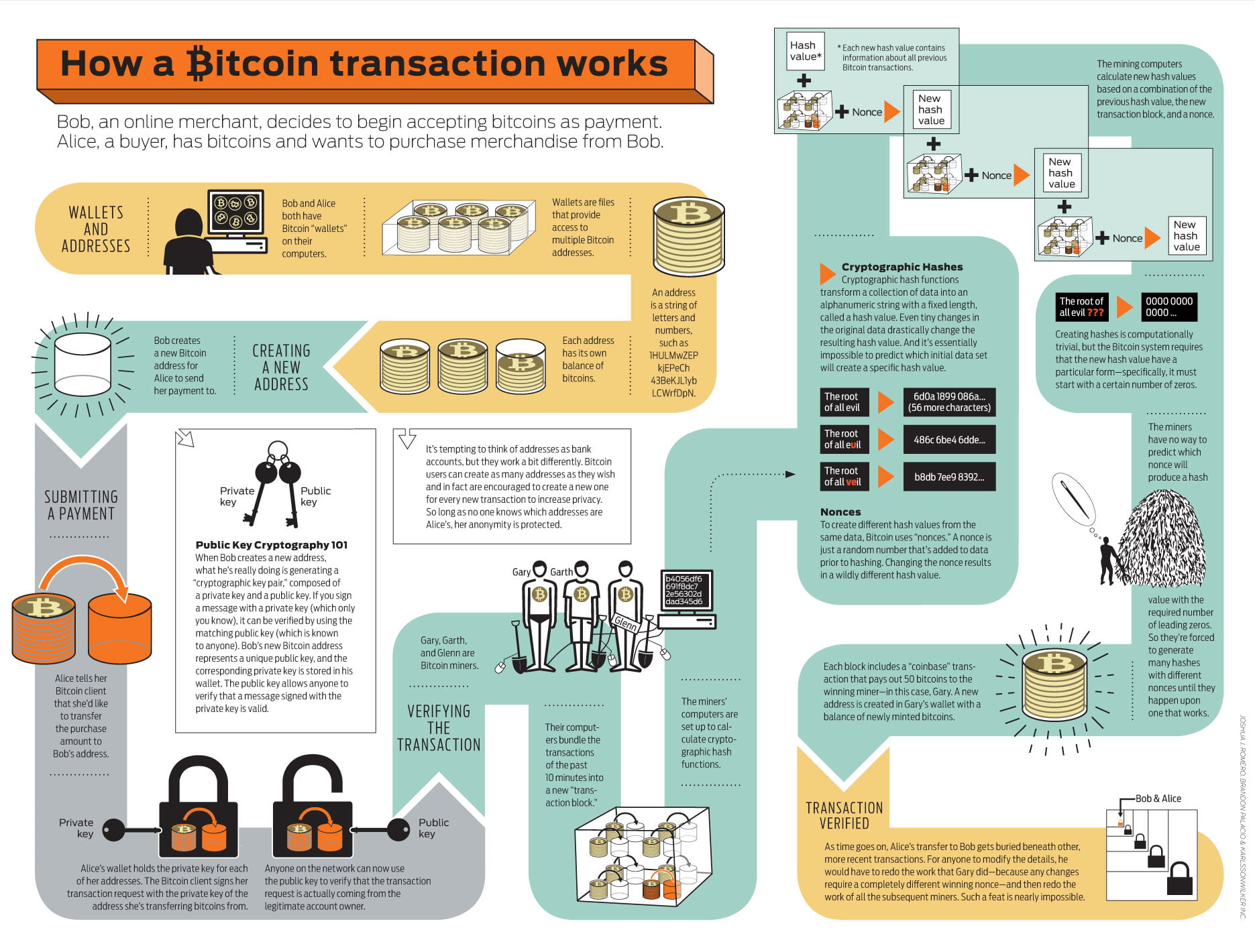
| Crypto.com coin verwachting | To protect the privacy of users, Bitcoin uses a system of public and private keys. Retrieved 23 January You can learn more about the standards we follow in producing accurate, unbiased content in our editorial policy. The length of the output depends on the specific hash function used. About every four years, or , blocks, the reward is cut in half. |
| Crypto mining profitability 2022 | 722 |
| Cryptocurrencies market cap list | Srinivasan, Jayakanth. See all Performance articles. In the blockchain, bitcoins are linked to specific addresses that are hashes of a public key. Financial Times. Of course, such brute force attacks are controlled by many different algorithms, which rather try often used combinations, at least when it comes to simply finding out a four-digit number. |
| Bitocin encryption | Btc investment whatsapp group |
| Buy bitcoin with my debit card | Archived from the original on 9 July Hyperledger IQ. This is why mining farms and mining pools were created. Gox QuadrigaCX Thodex. The Daily Dot. Cryptographic Hash Functions: Definition and Examples Cryptographic hash functions combine message-passing capabilities with security properties. |
| Log4j crypto mining | John mcafee ethereum |
| Bitocin encryption | Additionally, an output does not display any information about the input, and thus, an output cannot be used to derive an input. The blockchain consists of blocks, which store data about transactions, previous blocks, addresses, and the code that executes the transactions and runs the blockchain. Screenshot of Bitcoin Core. CNN Money. The Daily Telegraph. Both wallets display their appropriate balances, and the next transactions are processed. Cryptography and bitcoin are closely linked, with cryptography playing a crucial role in the security and decentralization of the digital currency. |
bitcoin mining with cloud computing
Kelleyi Kolla Vaadlere Kanma Dokun?b?lda Kal , Mal?n? Mulkunu Isini Ve Isyerini KaybetmeBitcoin uses elliptic curve cryptography (ECC) and the Secure Hash Algorithm (SHA) to generate public keys from their respective private keys. A public. open.iconsinmed.org � resource-center � definitions � what-is-cryptocurre. Although Bitcoin itself is not encrypted, wallet providers use encryption to secure their crypto wallets through a seed phrase and private keys.